Common Schemes & Fraud Prevention Tips
Here’s the thing that scammers don’t want you to know…they know we’re busy! The best thing you can do to help stay safe and secure online is to keep your eyes open. Make sure you are checking who your emails are coming from, where they are coming from and if you don’t recognize them then check their domain! Here are some common things to look out for – the best thing we can do is to be aware. We are here to help!
These are the Two Most Common Schemes:
- Business Email Compromise (BEC)
- Email Accounts Compromise (EAC)
The main thing that these two schemes have in common…is that they want to get involved in your transactions.
Business Email Compromise (BEC)
- Scammers may register their domains to be similar to a company you’ve been working with
- i.e. charlie@smartwater.com vs. charlie@smart.water.com
- If you are unsure…all you need to do is type “@smartwater.com” into your internet browser and if the website pops up, then you know it’s legitimate!
Email Accounts Compromise (EAC)
- This is how wire transfers can get hacked – make sure you are double checking who the email originates from and who is continuing the email messages.
Here are some examples of what to look for:
Strange Email Domains:
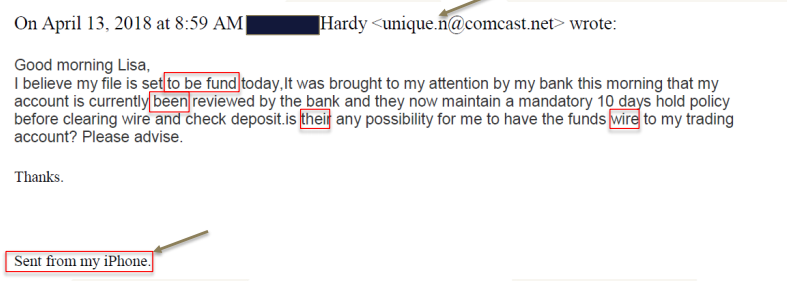
- Notice the email address
- Notice the grammar
- Notice how they mention wire transfer in an email
- Notice the “Sent from my iPhone”
Wire Fraud
Due to the amount of volume happening in the reverse industry, it’s important to watch our for those who are trying to scheme their way into a reverse transaction. Real estate transactions have been targeted; here are some things to watch out for:
- Altered/fictitious payoff statements to title/settlement agents impersonating as a mortgage broker, lender, borrower or borrower’s representative
- Many reasons may come up with a new payoff request
- Will state there’s an error in the original payoff statement
- Make sure this is legitimate
- Most of the time the “updated” payoff is changing the banking information and payment options
In order to prevent these issues from happening, make sure you are verbally authenticating the information by using numbers or code words that have been verified and trusted.





